Автор - Владислав Спектор
2009
OSI 7 layers model – создана организацией ISO в 1984 году (обратите внимание на инверсию слов ISO - OSI).
Формальное определение OSI: многоуровневое абстрактное представление и объяснение коммуникаций и дизайна протоколов компьютерных сетей.
Уровень (Layer) – это набор функций, которые обеспечивают сервисы вышележащему уровню и получают услуги от нижележащего уровня.
Сетевой протокол (Network protocol) — набор правил, позволяющий осуществлять соединение и обмен данными между двумя и более включёнными в сеть устройствами.
Для чего нужна модель OSI?
OSI – прекрасный способ изучения сетевой архитектуры. В любой области для решения сложной задачи ее раскладывают на составные элементы, которые поддаются решению. Сети и набор протоколов связи довольно сложны и разложение на уровни очень облегчает задачу объяснения и понимания проблемы.
Уровни также дают возможность создавать совместимые по интерфейсам (стандартным способам взаимодействия) и, в то же время, независимые протоколы, т.к. скрывают (наподобие черного ящика) технологии каждого уровня.
Как результат, производители протоколов и оборудования (сетевых карт, роутеров, свитчей и т.д.) получают возможность вместо одного протокола внедрить другой, более эффективный, не меняя при этом протоколы других уровней.
Например, на втором уровне вместо Ethernet можно использовать Token Ring или Frame Relay, а программы или вышележащие протоколы не будут об этом догадываться и продолжат работать как обычно.
Или, на физическом уровне, вместо медного кабеля можно использовать оптику или Wireless, а другие протоколы и программы не будут иметь об этом понятия.
В результате получается такой конструктор из слоев, где каждый слой-уровень можно заменять другими "деталями" без вреда для всей конструкции.
Пример из жизни: если у "Мерседеса" меняют коробку передач, не обязательно менять мотор или корпус, достаточно чтобы интерфейс между коробкой и другими "слоями" оставался тем же.
И, кстати, об интерфейсах: руль и педали – это пример интерфейса (стандартного способа взаимодействия) между человеком и машиной.
Вообщем, как всегда выигрывает стандартизация и взаимозаменяемость.
Ну, а поскольку сети рождены для соединения различного оборудования, средств передачи (media), протоколов, то стандартизация здесь важнее, чем во многих других областях.
А теперь настало время познакомиться непосредственно с самой моделью OSI. Кстати, она родилась в качестве теоретической и только потом были осуществлены попытки (не слишком удачные) внедрения ее в практику.
Рисунок
OSI 7 Layers Model
L7. APPLICATION L7. APPLICATION
L6. PRESENTATION L6. PRESENTATION
L5. SESSION L5. SESSION
L4. TRANSPORT L4. TRANSPORT
L3. NETWORK L3. NETWORK
L2. DATA LINK L2. DATA LINK
L1. PHYSICAL L1. PHYSICAL
>>>===========================>>>
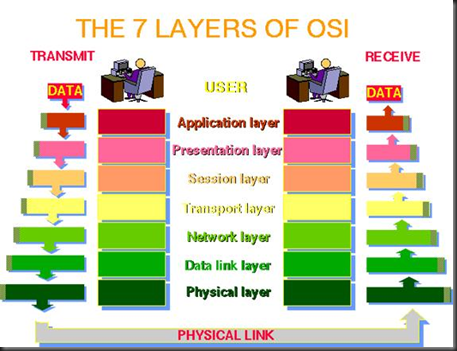
На рисунке схематически изображены уровни модели OSI, которых насчитывается 7.
Стандартный случай взаимодействия двух сетевых сущностей (компьютеров, роутеров и т.д.) таков: два хоста (компьютера, роутера и т.д.) заинтересованы создать логические коммуникации по горизонтали, т.е. между собой, с целью предачи информации.
С другой стороны, реальное взаимодействие происходит по вертикали, когда информация передается от какой-либо аппликации вниз по всем уровням (вертикально) и лишь затем транспортируется на другой хост (горизонтальное взаимодействие на уровне ниже первого).
Итак, по горизонтали мы имеем логические, виртуальные коммуникации при помощи протоколов, по вертикали – реальные, через связующие интерфейсы (для программистов замечу - API интерфейсы).
Теперь сравним дата-коммуникации с работой почты.
Представим себе писателя, который пишет роман и хочет передать его редактору для отзыва и правки (редактирования).
Рисунок
Layer7. APPLICATION - Писатель отдает роман секретарше
Layer6. PRESENTATION
Layer5. SESSION
Layer4. TRANSPORT - Секретарша делит роман на листы-сегменты
Layer3. NETWORK - Секретарша надписывает адрес
Layer2. DATA LINK - Секретарша бросает конверт в почтовый ящик
Layer1. PHYSICAL - Почта из почтового ящика передается почтальону
Layer0. Почтальон доставляет почту ====>>
Далее следует объяснение представленного рисунка.
Layers 7-6-5. Писатель (все три верхних уровня аппликаций) передает роман секретарше.
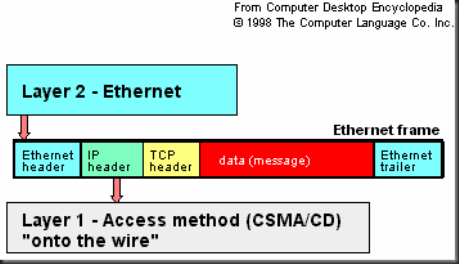
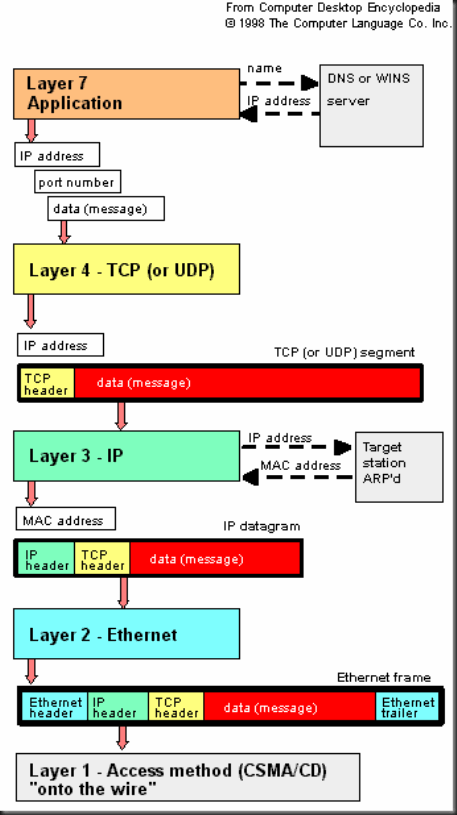
Layer 4. Секретарша (транспортный уровень) разделяет его на отдельные листы, вкладывает их в конверты, нумерует и надписывает имя адресата (при помощи протокола TCP поток данных разделяется на сегменты, каждый из которых получает последовательный номер, а также номер порта).
Layer 3. Следующая секретарша (сетевой уровень) надписывает адрес (протокол IP добавляет IP адрес в заголовок пакета).
Layer 2. Еще одна секретарша (уровень Data-Link) берет конверт и бросает его в почтовый ящик (передает фрейм сетевой карте). Кроме того в заголовок фрейма добавляется MAC-адрес ближайшего роутера (обычно в свойствах TCP/IP он называется Default Gateway), хотя реальный почтальон и сам знает, где находится ближайшее почтовое отделение.
На этом уровне взаимодействуют драйвер и сетевая карта.
Layer 1. Почта из почтового ящика (сетевой карты на физическом уровне) передается почтальону (средству передачи, например медному кабелю), который на велосипеде доставляет ее в почтовое отделение (сетевые импульсы от сетевой карты по кабелям локальной сети или другими средствами приходят на Default Gateway), которое распределяет все приходящие конверты-пакеты по месту назначения (роутинг) и перегружает их на соответствующий транспорт, движущийся в нужном направлении: машину, корабль, самолет, (медный или оптический кабель локальной сети, сериальный интерфейс глобальной сети, инфракрасное или микроволновое излучение, радио-излучение со спутников и т.д.).
В итоге роман прибывает в место назначения (другой хост) разными способами и путями.
Затем наш роман претерпевает обратный процесс подъема по коммуникативным уровням на другом хосте и, в итоге, попадает на стол редактору (или в нужную аппликацию). Обратите внимание, что писателя и редактора (уровень аппликаций) интересует только взаимодействие между собой (горизонтальное), хотя по техническим причинам им приходится пользоваться услугами помощников - нижележащих уровней (т.е. вертикальными взаимодействиями).
Кстати, сами компьютерные аппликации (Word, Internet Explorer и т.д.) находятся выше уровня аппликаций (L7), а передача по проводам или другим средствам коммуникаций, ниже физического уровня (L1).
Некоторые считают, правда, что средства коммуникаций находятся непосредственно на первом уровне, но мы будем придерживаться мнения таких авторитетов, как Эндрю Таненбаум, создатель системы MINIX (свободная Unix-подобная операционная система для студенческих лабораторий) и знаменитой книги по компьютерным сетям, которая стала фактическим стандартом в данной области.
В дальнейшем мы рассмотрим, что происходит на пути следования, но уже сейчас можно заметить, что информация периодически поднимается до 3-го уровня, и лишь в конце, на целевом хосте, она восходит на самый верх к своей цели. Обычно таковой является какая-либо программа.
Также, в дальнейшем, мы подробно разберем, что же происходит между 2-мя хостами, когда кто-либо пишет в адресной строке своего Internet Explorer: http://www.google.com
Правильный и полный ответ на этот вопрос является признаком хорошего осознавания сетевых процессов и определенного профессионализма.
Но, вернемся к нашим баранам :).
Модель OSI не является единственной моделью сетевых взаимодействий.
Из других, самая известная – модель TCP/IP.
Она отличается тем, что была создана на практике до создания теоретических обоснований. Как результат, она гораздо эффективнее в реальной практике, чем модель OSI и является сегодня стандартом De Facto.
Нужно сразу отметить, что TCP/IP - это и модель и набор действующих протоколов. Причем количество протоколов не два, как можно было бы предположить по названию, а гораздо больше.
В TCP/IP некоторые протоколы занимают сразу несколько уровней в нарушение строгих правил OSI, где каждому протоколу соответствует свой определенный уровень, который выполняет только ему отведенные функции.
В модели TCP/IP существует всего 4 уровня: группы 3-х верхних аппликативных и 2-х нижних модели OSI слиты каждая в единственный уровень модели TCP/IP, что уменьшает количество уровней и ускоряет процессы вертикальных коммуникации. Излишняя подробность OSI уменьшает реальную производительность, т.к. каждое взаимодействие между уровнями занимает время. Кроме того в OSI функции коррекции ошибок дублируются на 2 и 4 уровнях, что также отнимает время.
В то же время разбивка по слоям нужна и, даже, необходима. Можно, конечно, вообразить некий единый протокол, который будет простираться на все 7 уровней OSI. За счет отсутствия вертикальных взаимодействий между разными протоколами он будет, конечно, очень быстрым и никогда не возникнет проблем совместимости протоколов. Но это будет, так сказать, "одноразовый" протокол, т.е. им сможет воспользоваться лишь одна какая-то специфическая программа. В принципе, каждая программа, нуждающаяся в сетевых взаимодействиях, могла бы иметь свой собственный специализированный протокол. Как и каждый специализированный аппарат или программа, такой протокол мог бы быть чрезвычайно эффективным также и потому, что был бы совершенно лишен лишних универсальных функций, ведь универсальность добавляется, так сказать, "на всякий случай". Это напоминает эффективность DOS-овских игр, каждая из которых имела прямой доступ к железу компьютера и собственные драйверы (аналог протоколов). Эти игры работали очень быстро даже на слабом железе. Но мир почему-то все же отказался от такой эффективности в пользу универсальности. Уж очень она удобна и невероятно добавляет гибкости, а эффективность достигается другими способами, да и не во всех случаях эффективность стоит во главе угла, хотя и всегда принимается во внимание.
Существует также удобная 5-уровневая модель, которая является компромиссом между OSI и TCP/IP.
По аналогии с TCP/IP, три верхних уровня слиты в один - аппликативный, но 2 нижних (Phisycal и DataLink) разделены между собой так же, как и в модели OSI.
Добавoчные замечания
Интерфейс, протокол, драйвер, интерфейсная карта – важные понятия, которые существуют не только в сетях, но и в случае связи компьютера с периферийными устройствами.
Прозрачность Switches: на L1 все уст-ва прозрачны, на L2 SW прозрачны для комп., но комп. Видны свитчам, на L3 все видят друг друга.
На L2 действуют сетевая карта и ее сетевой драйвер.
MAC жестко хранится в NIC, а IP хранится в OS, поэтому MAC никогда не изменяется, а IP может изменяться каждый раз, например при помощи DHCP.
Routers – имеют CPU, который производит всю работу, а современные Switches имеют ASIC на каждом порту. Поэтому свитчи очень быстры.
ARP broadcasts запрашивают адреса IP, а NIC отвечающей стороны их не знает, поэтому ARP broadcasts поднимаются на уровень протокола IP и, соответственно, нагружают OS и CPU. В больших сетях, не разделенных роутерами или VLAN-ами, broadcasts способны значительно загрузить CPU всех комп. сети.
Роутеры также производят свитчинг (в общем понимании этого термина). Такой свитчинг 3-го уровня или Packet Switching называют Routing. Кроме Packet Switching существует Circuit (Channel) Switching.
Switching 2-го уровня производят свитчи и он называется Frame Switching. Это более знакомый нам вид свитчинга.
CSMA/CD нужен в случае Shared Media, коаксиальный кабель иначе работать не может. TS (twisted pair) дает принципиальную возможность отказаться от Shared Media и CSMA/CD за счет внедрения Switches.
![clip_image002[5] clip_image002[5]](http://lh5.ggpht.com/_HT3hWkseEbY/TDXdQjV5cTI/AAAAAAAAAA8/E8OSWTFrSVE/clip_image002%5B5%5D_thumb.gif?imgmax=800)
![clip_image004[5] clip_image004[5]](http://lh3.ggpht.com/_HT3hWkseEbY/TDXdSFo9OAI/AAAAAAAAABE/SsnV-xuY8mM/clip_image004%5B5%5D_thumb.jpg?imgmax=800)
![clip_image005[5] clip_image005[5]](http://lh6.ggpht.com/_HT3hWkseEbY/TDXdTaDb0mI/AAAAAAAAABM/D3yZ4KZzQpA/clip_image005%5B5%5D_thumb.jpg?imgmax=800)
![clip_image007[5] clip_image007[5]](http://lh3.ggpht.com/_HT3hWkseEbY/TDXdU4uqnvI/AAAAAAAAABU/zX6dwrAKAs4/clip_image007%5B5%5D_thumb.jpg?imgmax=800)
![clip_image009[5] clip_image009[5]](http://lh4.ggpht.com/_HT3hWkseEbY/TDXdWQs5kLI/AAAAAAAAABc/j2xN4JNz2dQ/clip_image009%5B5%5D_thumb.jpg?imgmax=800)
![clip_image011[6] clip_image011[6]](http://lh6.ggpht.com/_HT3hWkseEbY/TDXdXc4zE6I/AAAAAAAAABk/ywphQ7C4iyQ/clip_image011%5B6%5D_thumb.jpg?imgmax=800)